5 ways attackers can bypass two-factor authentication - Hoxhunt
Por um escritor misterioso
Last updated 18 junho 2024
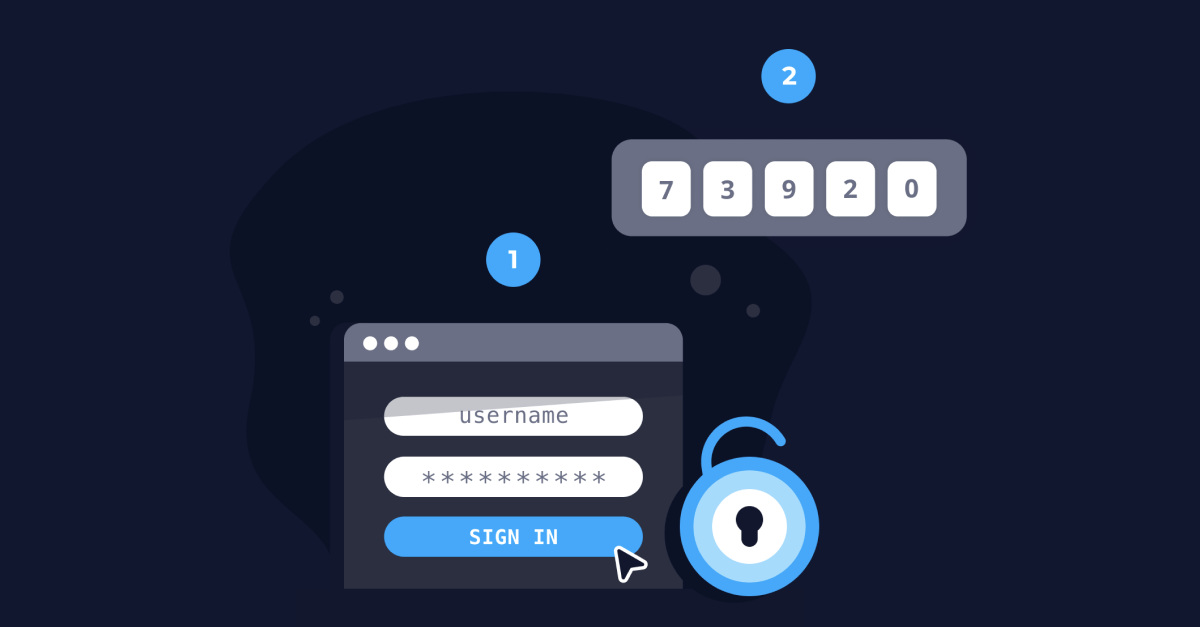
How Attackers Bypass Modern Two-factor Authentication and How to Protect Your Users

What happens if you lose your two-factor authentication login credential for Binance or Bitfinex? Is there any way to claim lost tokens? - Quora

Why Employees Remain Vulnerable To Harmful Phishing Emails

Mitigation strategies against the phishing attacks: A systematic literature review - ScienceDirect

How Attackers Bypass Modern Two-factor Authentication and How to Protect Your Users

How hackers bypass MFA and ways to stop them

Hoxhunt Reviews and Pricing 2023

The Power of ChatGPT: How ChatGPT is Changing the Phishing Game

How Attackers Bypass Modern Two-factor Authentication and How to Protect Your Users

How Hoxhunt minimizes cybersecurity risks from human error - Help Net Security

Mitigation strategies against the phishing attacks: A systematic literature review - ScienceDirect

Why Employees Remain Vulnerable To Harmful Phishing Emails
MFA Bypass 101

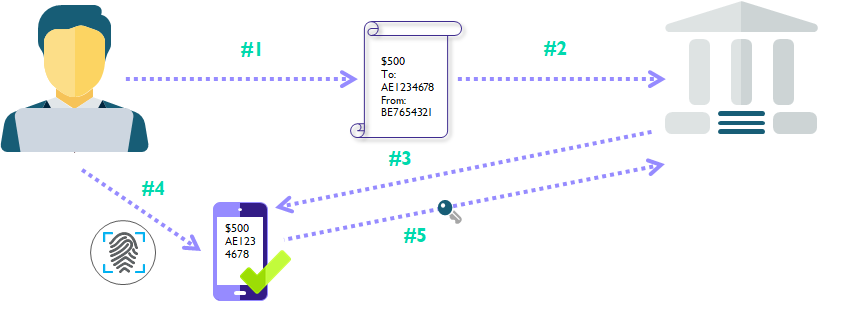
1. What is Two-Factor Authentication and 2. How hackers are using social engineering techniques to
Recomendado para você
-
 How To Create An Account on Roblox?18 junho 2024
How To Create An Account on Roblox?18 junho 2024 -
 5 FREE ROBLOX ACCOUNTS WITH ROBUX *PASSWORDS IN18 junho 2024
5 FREE ROBLOX ACCOUNTS WITH ROBUX *PASSWORDS IN18 junho 2024 -
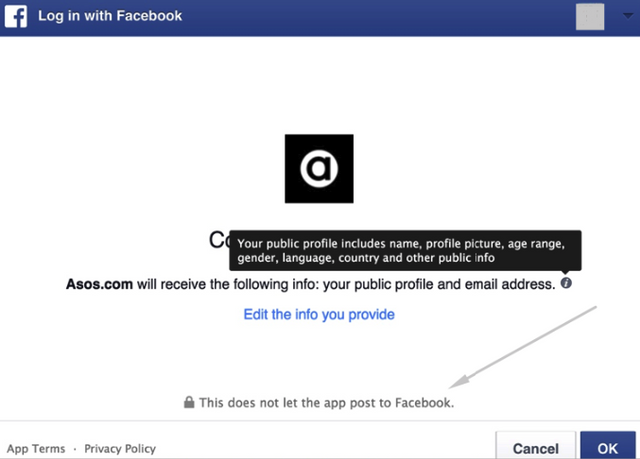 Does Your Store UX Need a Facebook (Meta) Login Option?18 junho 2024
Does Your Store UX Need a Facebook (Meta) Login Option?18 junho 2024 -
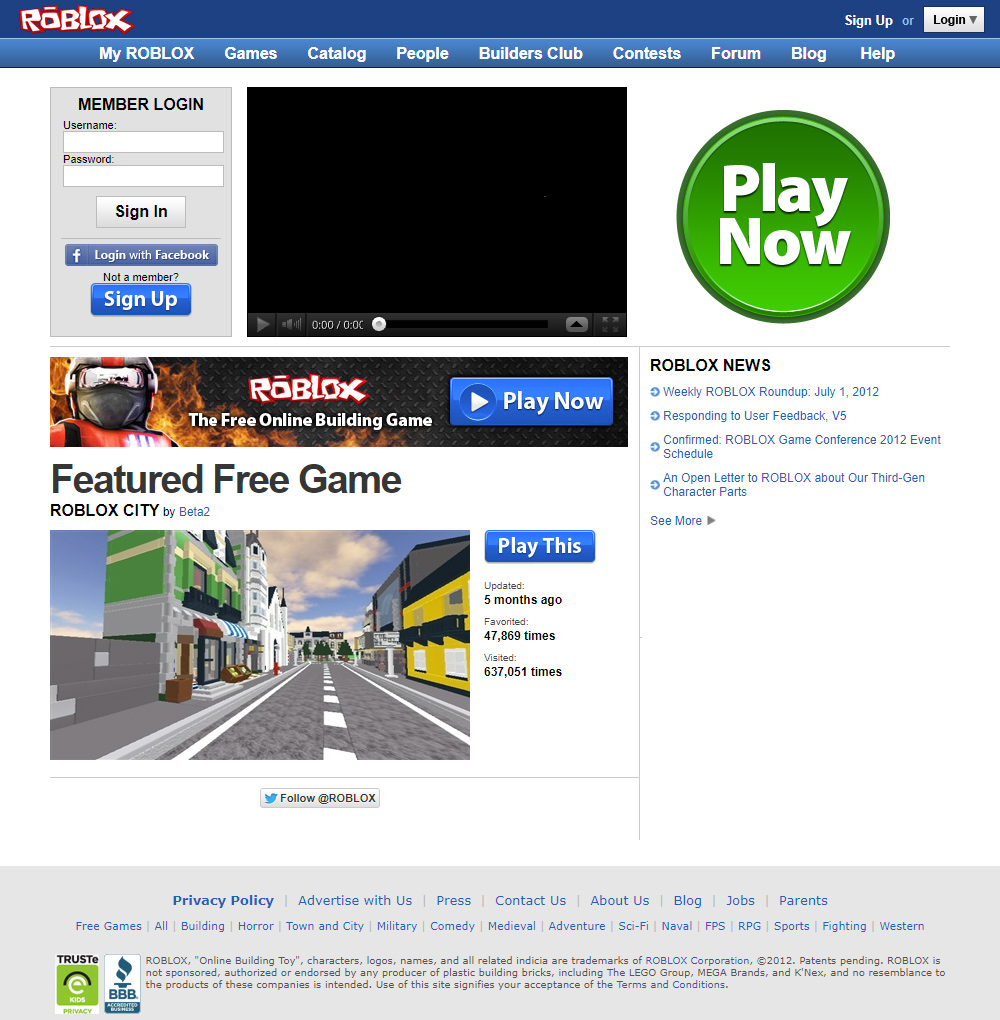 Roblox in 2012 - Web Design Museum18 junho 2024
Roblox in 2012 - Web Design Museum18 junho 2024 -
free robux group roblox Public Group18 junho 2024
-
 How to Recover Roblox Account Without Password or Email18 junho 2024
How to Recover Roblox Account Without Password or Email18 junho 2024 -
Roblox - How to play roblox18 junho 2024
-
Roblox Top-up PH - NEW PROMO CODE Claim your Socialsaurus Rex with18 junho 2024
-
 permissions - Firebase Facebook oAuth missing scopes in Facebook18 junho 2024
permissions - Firebase Facebook oAuth missing scopes in Facebook18 junho 2024 -
 RECOVER Roblox PASSWORD w/o EMAIL for FREE! - IamSanna, Jelly18 junho 2024
RECOVER Roblox PASSWORD w/o EMAIL for FREE! - IamSanna, Jelly18 junho 2024
você pode gostar
-
 Tengen Toppa Gurren Lagann (Manga), Tengen Toppa Gurren Lagann Wiki18 junho 2024
Tengen Toppa Gurren Lagann (Manga), Tengen Toppa Gurren Lagann Wiki18 junho 2024 -
 Shingeki! Kyojin Chuugakkou Wallpapers - Wallpaper Cave18 junho 2024
Shingeki! Kyojin Chuugakkou Wallpapers - Wallpaper Cave18 junho 2024 -
 Italia U20, delusione Mondiale: l'Uruguay nel finale beffa gli azzurri18 junho 2024
Italia U20, delusione Mondiale: l'Uruguay nel finale beffa gli azzurri18 junho 2024 -
 Connie Talbot Net Worth18 junho 2024
Connie Talbot Net Worth18 junho 2024 -
 Burnley beat Luton 2-1 for first league win of the season18 junho 2024
Burnley beat Luton 2-1 for first league win of the season18 junho 2024 -
 Soma Yukihira, anime, food wars, guys, new anime, HD phone18 junho 2024
Soma Yukihira, anime, food wars, guys, new anime, HD phone18 junho 2024 -
 Mushoku Tensei: Jobless Reincarnation Season 2 Episode 8 Release18 junho 2024
Mushoku Tensei: Jobless Reincarnation Season 2 Episode 8 Release18 junho 2024 -
 Apple Will Scan U.S. iPhones For Images Of Child Sexual Abuse : NPR18 junho 2024
Apple Will Scan U.S. iPhones For Images Of Child Sexual Abuse : NPR18 junho 2024 -
![fnf Zanta Alphabet Lore - G U N Vs. F [Friday Night Funkin'] [Mods]](https://images.gamebanana.com/img/ss/mods/63b73d741159e.jpg) fnf Zanta Alphabet Lore - G U N Vs. F [Friday Night Funkin'] [Mods]18 junho 2024
fnf Zanta Alphabet Lore - G U N Vs. F [Friday Night Funkin'] [Mods]18 junho 2024 -
 Four Retro Games Worth Checking Out on Nintendo Switch Online - Old School Gamer Magazine18 junho 2024
Four Retro Games Worth Checking Out on Nintendo Switch Online - Old School Gamer Magazine18 junho 2024

